The last post was very long and a bit crazy all over the place, but here we are continuing with it. To illustrate how to crate a destination NAT, we will be opening FTP to one of our DMZ server, so lets get started
Create Object
Under Objects -> Services we will create our new FTP Object

Destination NAT Policy
We are pretty much following the same flow we initially followed when we were playing with the Source NAT Policies, with few minor changes that will make sense
General TAB
* Name
* Tags
* Group Rules by Tag
* Audit Comment

Original Packet
* Source Zone
* Destination Zone
* Destination Interface
* Service
* Destination Address

Translated Packet
* Translation Type
* Translated address
* Translated Port


*** It’s different the way NAT is done in PANOS, but I guess it takes time to accommodate and understand how it works, the destination address translation is what really triggers the actual NAT, in this case notice that we don’t change anything from our Source Address Translation.
** I want to add a disclaimer, in all honesty – I noticed that the LAB specifies 192.168.1.1 as the destination and I was a bit worried, because the flow of the NAT policy did not make sense to me, so we are translating basically the GatewayIP to the DMZ Server IP on Port 20-21
** Sometimes it takes doing to understand the concepts.
Security Policy
* General Tab

* Source Tab

* Destination Tab

* Service/URL Category

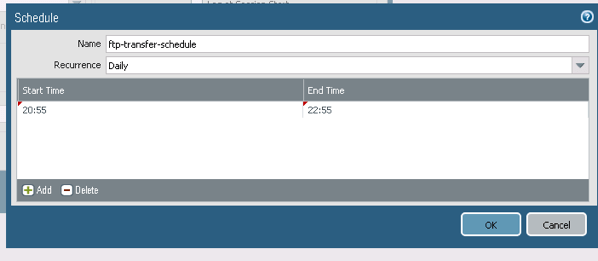
We are going to spice it up and we are going to add a Schedule to this port to be open
Adding a Schedule to a Security Policy
By default all security rules are always in effect, but this setting under the Actions Tab allows us to create a Schedule – Under Actions, select Schedule and Create a new Schedule

About the Author:
Andres Sarmiento, CCIE # 53520 (Collaboration)
With more than 15 years of experience, Andres is specialized in Unified Communications and Collaboration technologies. Consulted for several companies in South Florida, also Financial Institutions on behalf of Cisco Systems. Andres has been involved in high-profile implementations including Cisco technologies; such as Data Center, UC & Collaboration, Contact Center Express, Routing & Switching, Security and Hosted IPT Service provider infrastructures.

